Global DDoS
protection service
All-in-one real-time DDoS protection for websites, apps, and servers.
Server protection
Protecting servers against DDoS attacks at the network (L3), transport (L4), and application (L7) layers in data centers around the world.
Network Protection
Protect your datacenter with Protected IP Transit service
How our filtering platform works
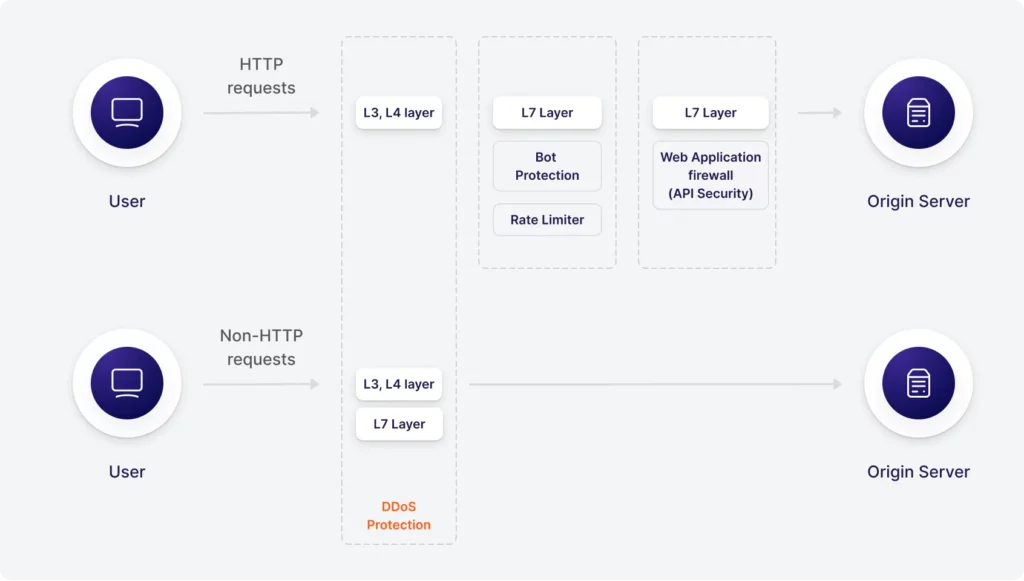
The Computer.Com security platform consists of our own scrubbing centers around the world.
The scrubbing centers are connected to several service providers and have backup copies of all systems, such as cleaning servers, managing servers, data storage systems, and network equipment.
The Computer.Com security platform guarantees no delays and no performance degradation for your digital business.
Your users and customers won’t even notice that your web resource has been attacked.
The types of DDoS attacks we protect against
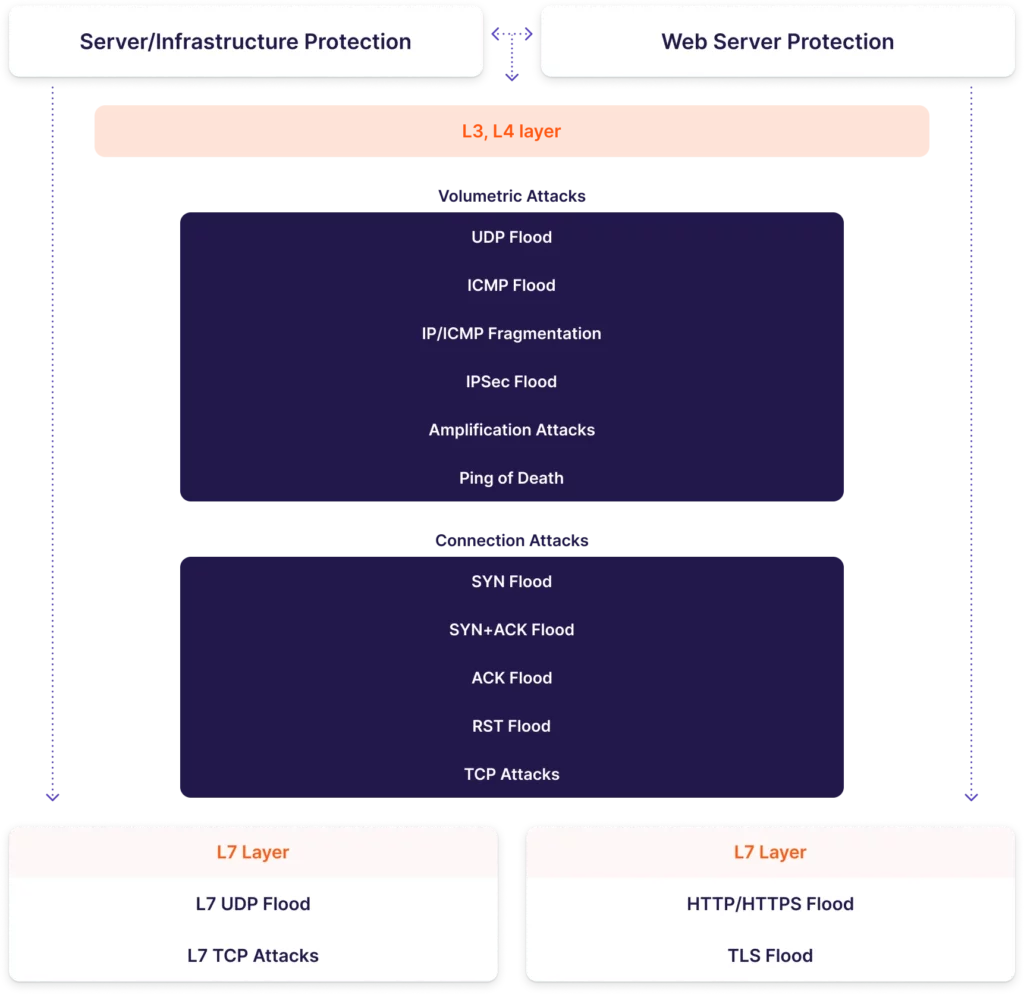
Cyberattacks are becoming more complex and multi-vectored:
Network-layer DDoS attacks sap networks’ bandwidth and disrupt the target’s interactions with partners and clients.
Connection-layer DDoS attacks overload a server with a large number of TCP packets (typically with the SYN/RST/ACK/PSH messages) to consume all its available resources.
Application-layer DDoS attacks interfere with or even completely paralyze the operation of business applications, which causes huge material and reputational losses for the targets.
To learn more, please read our radar report “DDoS attack trends”
Advanced protection features
Proprietary DDoS protection solution
Low-frequency attacks detection from the first query
False positive rate is less than 0,01%
Real-time statistics in the control panel
Server protection in your data center through the GRE tunnel
24/7, high-qualified technical support
Threats of losses when DDoS attacks happen
Loss of profits
Your losses are easy to calculate: the inaccessibility of the resource per hour equals your earnings per hour.
Loss of customers’ data
Often, a DDoS attack can be only a part of a larger attack to steal users’ personal data.
Loss of loyalty
The Internet has empowered users to leave negative reviews on the web, and those reviews will take away your new customers.
Loss due to compensation
If your project is a SaaS, be prepared to compensate your customers if your service is unavailable.
Use cases in demand
Fintech industry
E-commerce
Gaming industry
~80% of the attacks are on game servers. Once you fail, you risk losing your reputation and customer loyalty forever.
Learn more about our game server protection expertise.
SaaS companies
Plans
To estimate the cost of the project, tell us in detail about the infrastructure that needs protection.
Prices are shown minus VAT.
Connect DDoS Protection

By clicking the button you give us an informed, specific and unambiguous consent to process your personal data in accordance with our Privacy policy
