Web Application Penetration Testing
A pen test trial for IT infrastructure and web applications.
Its goal is to simulate a possible attack and determine how deep an attacker can penetrate the system, and how much damage can be caused to a business.
Through this, we can identify existing vulnerabilities and assess the current information security risks.
We test two scenarios: external penetration (when the access rights to the application are not available), and internal actions of company employees who have access rights.
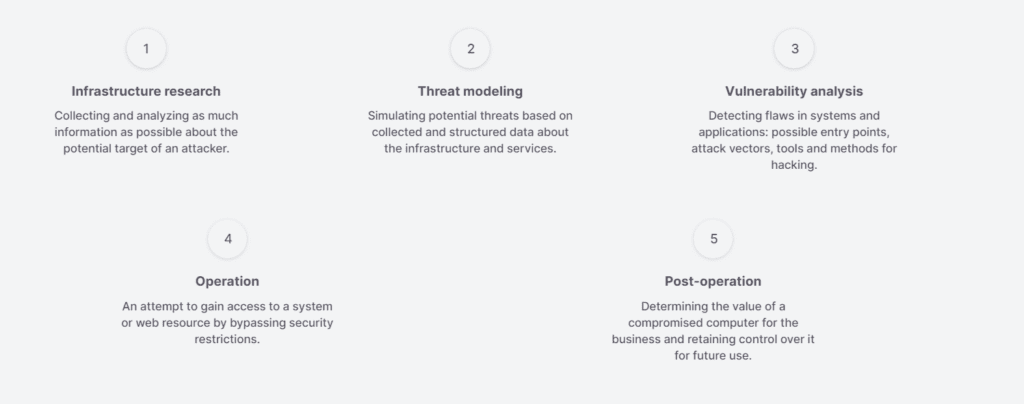
Five stages of penetration testing
Testing is based on the OWASP Web Security Testing Guide and Penetration Testing Execution Standard and includes five main stages.
What the pen test results report includes
- Testing summary and checklist
- Methodology
- Current security threats
- Detailed description of vulnerabilities detected
- Recommendations for enhancing the infrastructure and web services security

How we describe detected vulnerabilities
CVSS evaluation
Attack replay scenarios
Possible consequences of attacks
Recommendations on how to fix vulnerabilities
Contact us to get a
personalized offer

