Web Application Security
Get your web applications and services protected against DDoS attacks (L3, L4, L7), hacking threats and malicious bot activities with an all-in-one web security solution by Computer.Com.
Security features

Keep your service available even under the strongest attacks
Stay focused on your primary business and not on web security fortifications
Protect your application from different attack vectors without harming performance
Save money by avoiding costly web filtering and network appliances
Security features
Globally distributed network to filter all traffic around the world
Our growing distributed network capacity will always exceed any single DDoS attack
Protect against low-rate attacks from their first request
Advanced load balancing algorithms for better availability
False positive rate is less than 0.01%
Block malicious sessions, not IPs

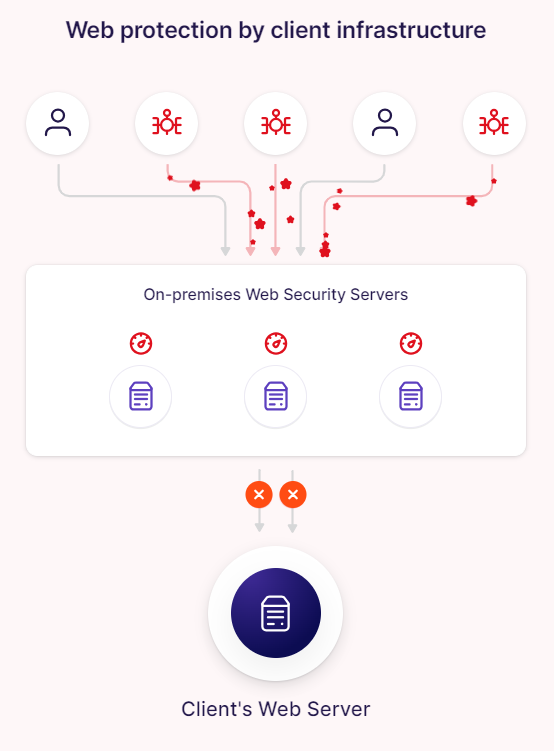
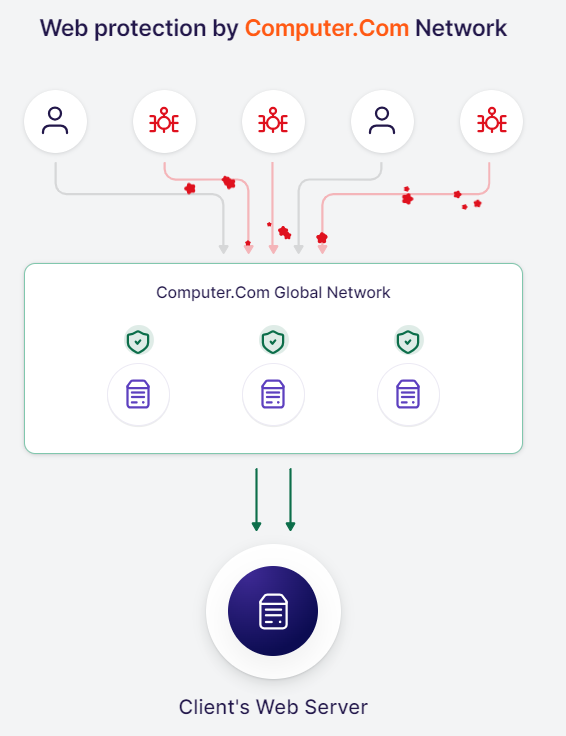
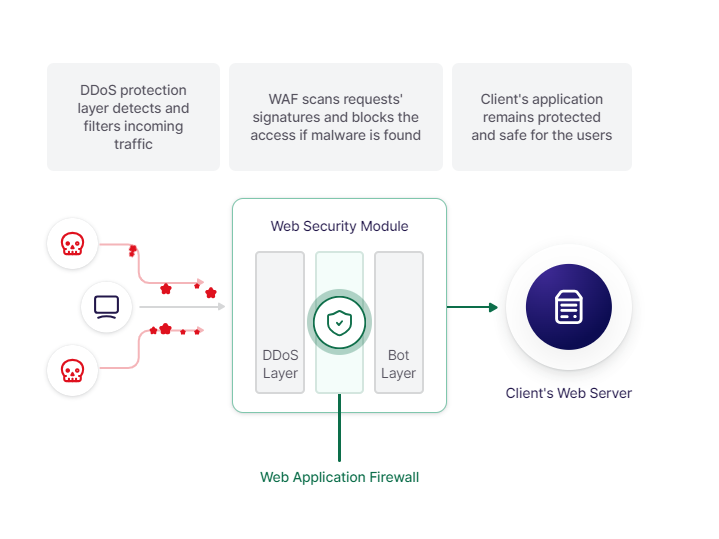
Web Application Firewall
- Prevent user credentials theft
- prot service from unauthorized access
- Reduce the risk of personal data leaks
How WAF works
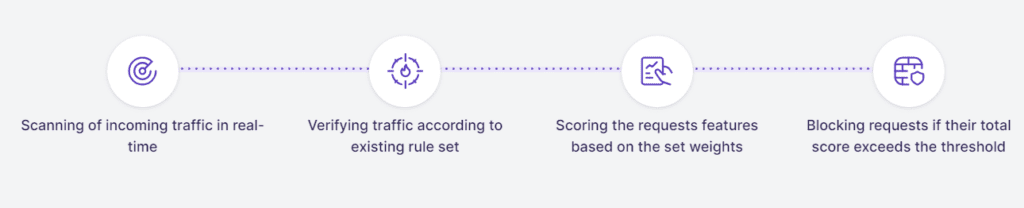
Protect from different hacking attacks:
Cross-Site Request Forgery (CSRF)
Cross-Site Scripting (XSS)
Local File Inclusion (LFI)
Remote File Inclusion (RFI)
SQL Injection (SQLi)
Other OWASP Top 10 threats
API security
- JSON-based APIs (including CRUD, REST, and customs APIs)
- SOAP APIs
- XMLRPC and customs XML-based APIs
- Open Banking APIs

API security
- JSON-based APIs (including CRUD, REST, and customs APIs)
- SOAP APIs
- XMLRPC and customs XML-based APIs
- Open Banking APIs
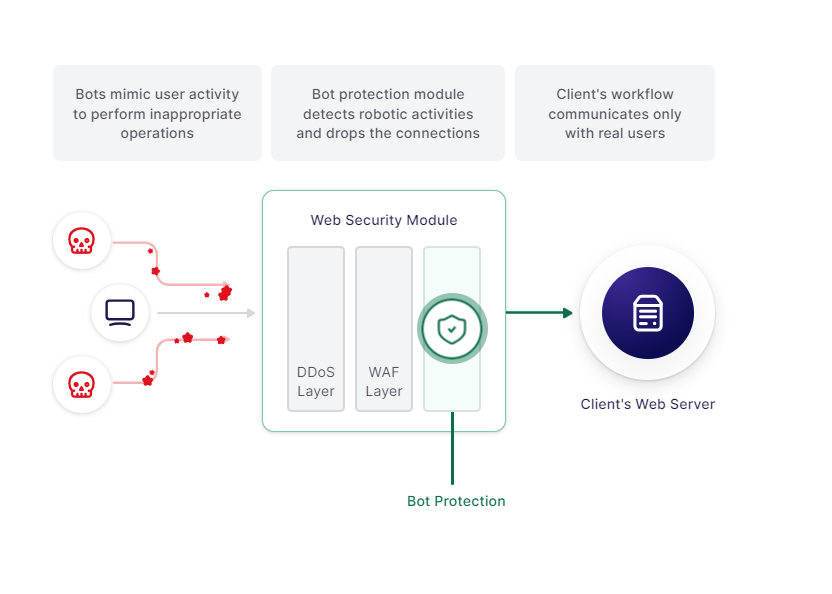
Bot protection
Bot protection prevents online services from overloading and keeps your business workflow running smoothly.
- Mitigate website fraud attacks
- Eliminate request form spamming
- Prevent brute-force attacks
Protect from different bot activities:
Web Content Scraping
Account Takeover
Form Submission Abuse
API Data Scraping
TLS Session Attacks
Plans
ENTERPRISE
Custom
For small business websites
* Legitimate traffic (billable traffic) is prevailing clean traffic (usually incoming traffic from a client). The average bandwidth of incoming and outgoing clean traffic is calculated separately every minute (Mbps). Statistics for the month are collected and 5% of the highest values are discarded (36 hours). Then the maximum figure for each direction is weighted (95th percentile). The larger of these two figures is the bandwidth of legitimate (billable) traffic.
Prices are shown minus VAT.
